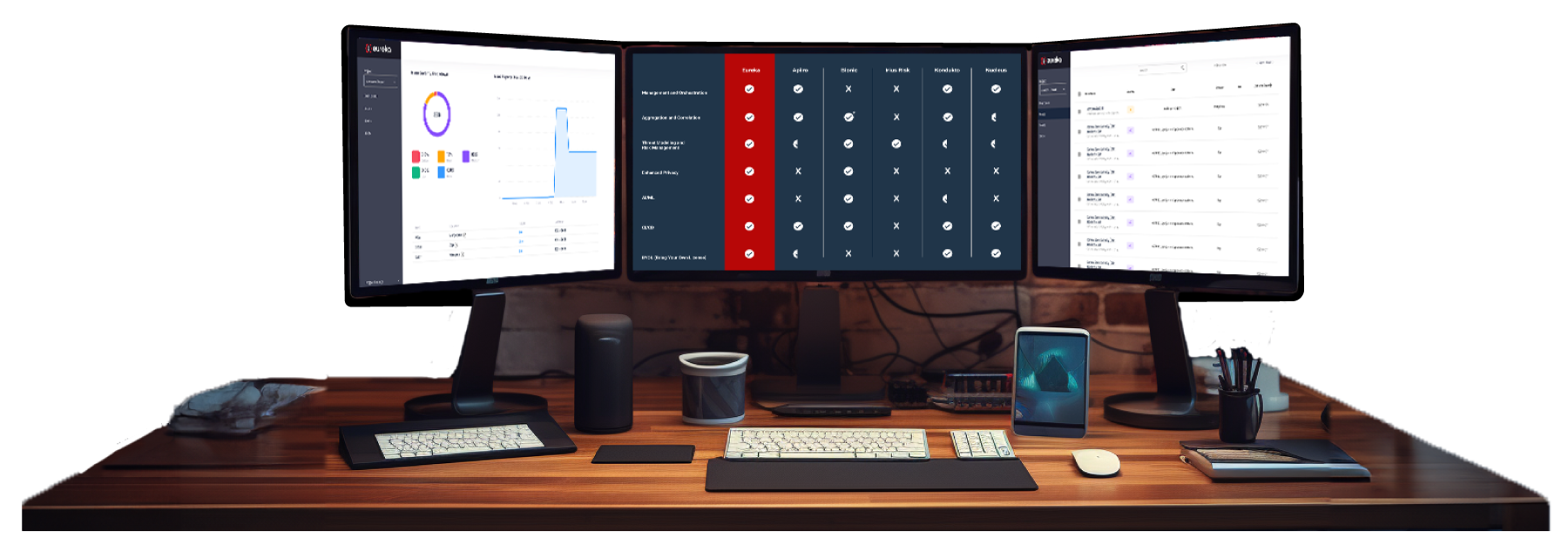
Comparison
Accelerate your DevSecOps
| Management and Orchestration | ❌ | ❌ | ❌ | |||||||
| Aggregation and Correlation | Partial | ❌ | Partial | |||||||
| Threat Modeling and Risk Management | No threat modeling | No threat modeling | Partial | No threat modeling | No threat modeling | No threat modeling |
||||
| Enhanced Privacy | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | ❌ | |||
| AI/ML | ❌ | ❌ | Partial | ❌ | ❌ | |||||
| CI/CD | ❌ | ❌ | ||||||||
| BYOL (Bring Your Own License) | Partial | ❌ | ❌ | Partial | ❌ | Partial |
Management and Orchestration
Management involves the central configuration and maintenance of multiple scanning tools in one platform.
Orchestration is the coordination and execution of different security scanners from a single docker container. All scanners are in one agent and running in one place.
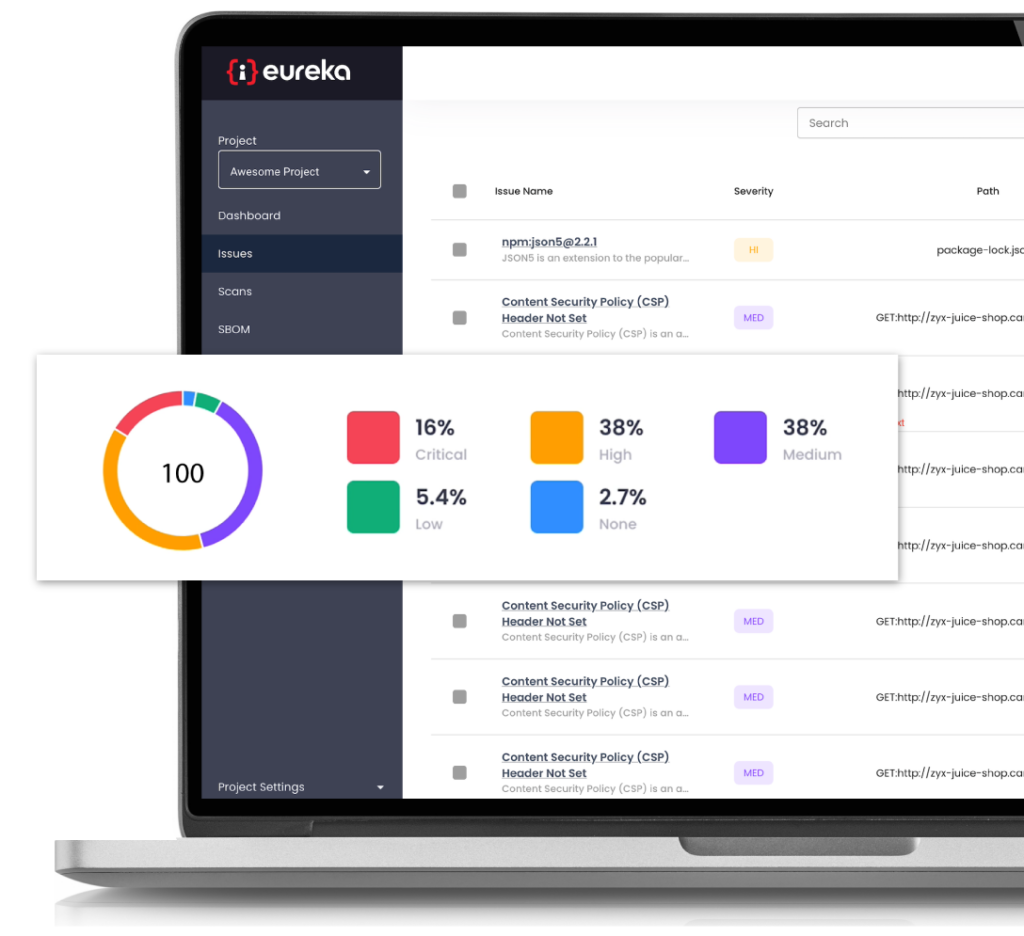
Aggregation and Correlation of Results
Aggregation is the act of combining or normalizing results from multiple scanners into one place to create a more concise and easier to understand view.
Correlation refers to identifying meaningful relationships, patterns, or similarities among various data points and grouping them together.
Threat modeling and Risk Management
Threat modeling is a structured and systematic approach to identifying, evaluating, and mitigating potential threats and vulnerabilities in a system or application. In our context, Eureka finds vulnerabilities that when combined, can form a threat scenario and provide the attacker with the necessary steps to exploit the application.
Risk management involves the identification and control of risks. Eureka assigns risk levels to potential threats based on their impact on the business system, which is determined by contextual information and the likelihood of vulnerabilities being exploited.
Enhanced Privacy
Privacy is the promise made to the client about protecting their personal and sensitive data. Eureka takes this to another level with enhanced privacy. Eureka stores all client data in a client-owed environment, so they are always in full control. We never see your data, nor do we ever have access to it.
AI/ML
AI (Artificial Intelligence) is the capability of machines to mimic human intelligence, enabling them to perform tasks like learning, reasoning, and problem-solving.
ML (Machine Learning) is a subset of AI focused on computer learning and improving tasks from data without explicit programming. In the context of Eureka, we will be using AI/ML to improve software security by reducing false positives and better define threat scenarios.
CI/CD
Continuous Integration/Continuous Deployment (CI/CD) is a set of practices and tools used by software development teams to automate the building, testing, and deployment of software applications. Security scanners can be integrated into pipelines to automate the process, and Eureka makes this easier.
